Asset security
A clear view of your OT assets is the first step toward a secure and resilient industrial network

As the Industrial Internet of Things (IIoT) grows, traditional asset discovery methods—like ping sweeps and manual inventories—fall short. These outdated techniques lack precision and fail to map device relationships, leaving critical blind spots. For IT and OT leaders, enhancing asset visibility is essential to strengthen industrial asset security and reduce vulnerabilities in cyber-physical systems (CPS).
A recent survey shows that 32% of organizations experienced both IT and OT disruptions during a cyberattack—up from 21% the year before. This highlights the urgent need for advanced OT asset discovery, which forms the foundation of any robust industrial cybersecurity strategy and enables effective, proactive security controls.
Start your road to success with our Saas products
Operational Technology (OT) refers to the hardware and software used to control and monitor industrial processes. OT asset discovery is a method for gaining visibility into these networked systems, providing a detailed inventory of assets without disrupting operations. Unlike traditional IT asset discovery, which is designed for uniform environments, OT asset discovery must accommodate a diverse and often outdated ecosystem of devices.
Using passive network scanning, OT asset discovery can detect:
- IP addresses
- Port numbers
- MAC addresses
- Firmware versions and configuration details
This information enables organizations to map and inventory assets, strengthening their cybersecurity posture.
You can’t secure what you don’t know exists. OT asset discovery is the first step toward industrial cybersecurity.
IT vs. OT Asset Discovery
IT asset discovery and OT asset discovery require different approaches due to the unique characteristics of OT environments:
- IT environments have assets with commonalities, frequent replacements, and standardized software.
- OT environments consist of specialized assets with varying makes, models, and software versions—some operating for decades without updates.
This complexity necessitates an OT-specific discovery approach to ensure accurate visibility and security.
Why Do You Need OT Asset Discovery?
The importance of OT asset discovery cannot be overstated:
-
Visibility: “You can’t protect what you can’t see.” Mapping and inventorying assets is crucial.
-
Security: Protect OT assets from malware, ransomware, and insecure remote access.
-
Operational Efficiency: Prevent downtime and ensure business continuity.
-
Compliance: Meet industry regulations such as NIS2, NERC-CIP, and SOCI.
A well-known example of the risks of poor OT security is the Colonial Pipeline ransomware attack, which caused widespread fuel shortages and financial losses in 2021.
5 Steps to Gain Visibility for Your OT Network Assets
1. Identify OT Assets
Asset discovery must go beyond basic details, providing:
Device model and firmware version
Configuration information
Network connections and dependencies
With this data, organizations can create an accurate asset inventory for effective security management.
2. Map Out Network Topology With 3-D Visibility
Understanding user activity, asset communication, and connectivity paths is essential for operational resilience. Implementing 3-D network topology visualization enhances threat detection and incident response.
3. Combine Active and Passive Scanning
A hybrid approach improves asset discovery:
Passive monitoring collects data without disrupting operations.
Active queries extract deeper insights using device-specific protocols.
By combining these methods, organizations can achieve a more granular view of their OT environments.
4. Utilize OT-Specific Discovery Models
Claroty’s AppDB (Application Description Database) enhances asset discovery by:
Providing detailed protocol, device, and application information
Parsing backup configuration files for precise visibility
Discovering assets even when disconnected from the network
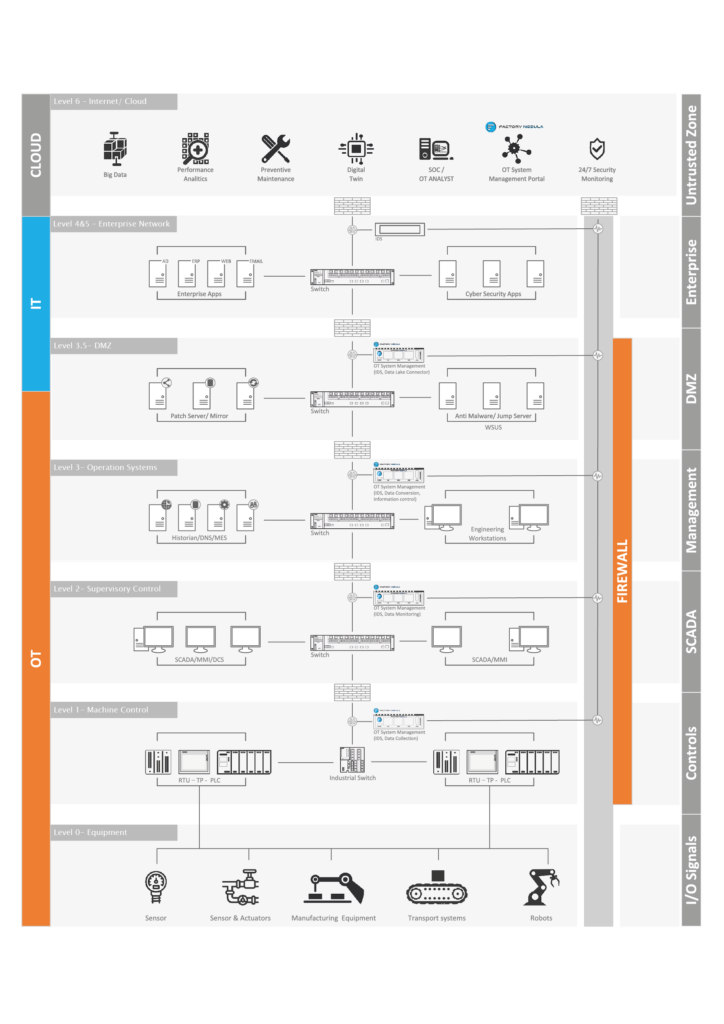
5. Implement Network Segmentation
Network segmentation enhances security by controlling asset communication. The Purdue Model categorizes industrial control systems into security zones, reducing attack surfaces.
Conclusion: The First Step to Securing the OT Environment
OT asset discovery is the cornerstone of a secure industrial network. By implementing these five steps, organizations can protect critical infrastructure, ensure business continuity, and stay ahead of cyber threats.
Partner with Claroty for the most comprehensive OT cybersecurity solutions. Request a demo today to strengthen your asset discovery strategy.








